Skill Assessment in Introduction to Malware Analysis
Hi again! This is my next write-up, and this time I’m covering the Skill Assessment section of the Introduction to Malware Analysis module.
It is quite difficult, and I had some trouble figuring out the answers (especially the last one).
So I hope my write-up will help some people who got stuck (I’m still learning, so some of my methods might be weird though).
Preparing the Environment
First, we need to download the malware sample. I used my VM to access the HTB file since if you use your regular Windows machine, there is a high chance the download will be blocked.
Tasks
Task 1
This one is a warm-up, so relatively easy.
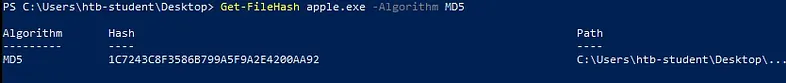
After downloading and extracting apple.exe, we just need to use:
On Linux VM:
md5sum apple.exe
On Windows VM (using PowerShell):
Get-FileHash apple.exe -Algorithm MD5
Make sure you are in the same folder as apple.exe.
Task 2
I found a good guide explaining packeting and obfuscation, and the short answer is “No”, since there are no signs of packeting in the given sample.
Task 3
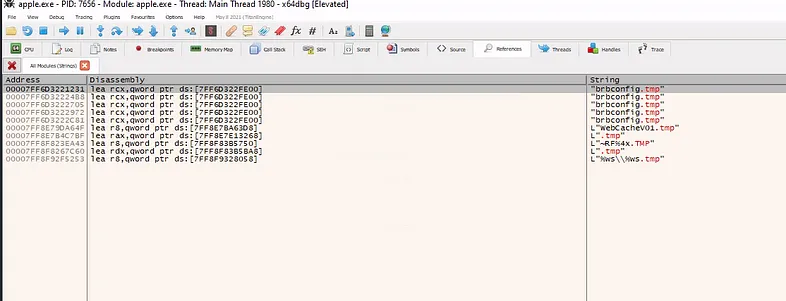
There are multiple ways to solve this task. Since we already know the file extension, the easiest method is using the strings command or a similar approach in PowerShell:
On PowerShell:
Get-Content apple.exe | Select-String -Pattern ".tmp"
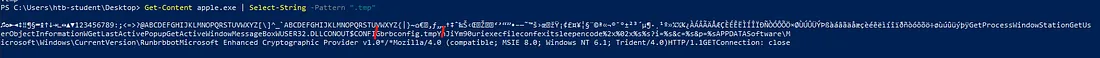
You will see the answer in the output.
Alternatively, we can use x64dbg:
- Start the program from the Tools directory on the desktop of the Windows VM.
- Open
apple.exe. - Search for all string references that include
.tmp.
Task 4
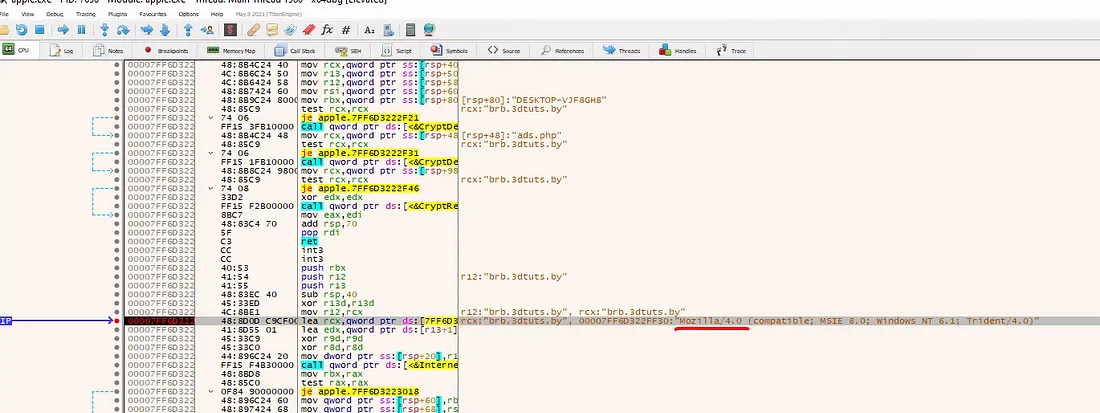
This took a bit of time to figure out, but eventually, all we need to do is:
- Set up a correct breakpoint.
- Run the code to the section.
In my case, I:
- Put a breakpoint (press
F2or right-click and select Breakpoint → Toggle) on the user agent string that I found using strings reference search. - Press
F4or select Debug → Run to Section to execute the code.
You will see the domain.
Task 5
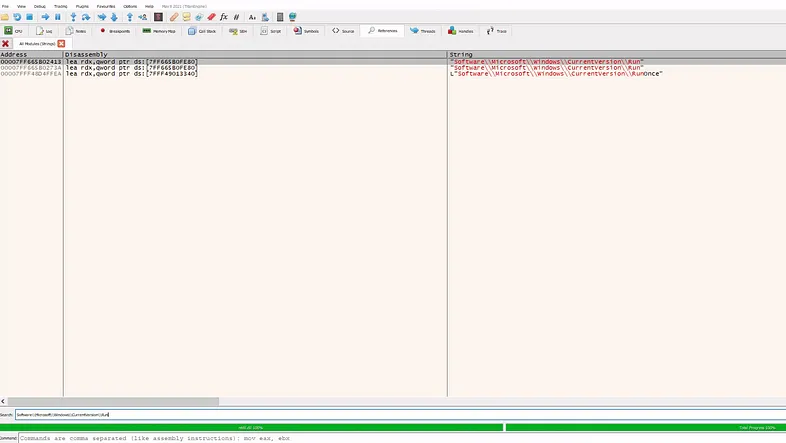
This one is relatively easy. We can just search for the registry key using strings reference search like before.
Just remember to use double slashes (\\) instead of single slashes (\).
Task 6
This was a tough nut to crack. The hint didn’t help much, although finding the ReadFile function and setting a breakpoint is not that complicated.
After some research, I found that there are two DLLs often used for encryption on Windows:
advapi32.dllcrypt32.dll
Both of these are used in apple.exe. If we go to the Symbols tab and select advapi32.dll, we will see the function we need in the list.
This function is also used in cryptsp.dll.
I managed to get the encrypted content of the .tmp file after setting a breakpoint on advapi32.dll → CryptDecrypt function. However, it seemed that I could get similar results by placing a breakpoint on the ReadFile function as well, so it wasn’t that straightforward.
Final Thoughts
It was quite an interesting module. However, I would recommend doing a separate course on malware analysis and reverse engineering since this module only scratches the surface.
I recommend going through the TCM Security Practical Malware Analysis course. I bought it some time ago, and it is in my to-do list.
Good Hunting!